What is Triangulation Fraud? How to Defend Against Reseller
Scams
Consider the perfect eCommerce sale. An honest customer buys a product online that the merchant fulfills. The merchant earns business revenue, while the customer receives a needed good or service. Everyone is happy. Unfortunately, fraudsters have developed ways to insert themselves into this process: as fake middlemen. Since many merchants act as resellers, drop shippers, or third-party suppliers on eCommerce platforms, criminals can create businesses that lure unsuspecting consumers into three-way fraud—a scam known as triangulation fraud. Triangulation fraud has devastating impacts on merchants. It leads to direct financial losses, chargebacks, product loss, and drained resources. Even worse, the scam preys on the privacy and trust of digital sales, leading to a crucial breakdown of faith by the consumer in the payments industry. FUGU has post payment defenses that give you more time to accurately detect and limit this type of fraud. Let’s explore triangulation fraud and how you can protect your business from this scam.
Triangulation Fraud Explained
Triangulation fraud is a social scam (typically within a card-not-present ecosystem) that creates a false version of a triangular sale. A fraudster, posing as a business or reseller, accepts money from unsuspecting consumers. They mirror common three-way sales that you might see, say with travel agents or event ticket resellers, but instead of filing orders honestly, they use false orders with merchants.
The tactic tricks both the customer and merchants into completing what looks like honest sales. In reality, the genuine parties have engaged with a false middleman (one who pockets the money and leaves the merchant with the chargeback). The triangular nature of the scam comes from the fact that three parties are conducting the sale: the genuine customer, the fraudulent seller, and the honest merchant.
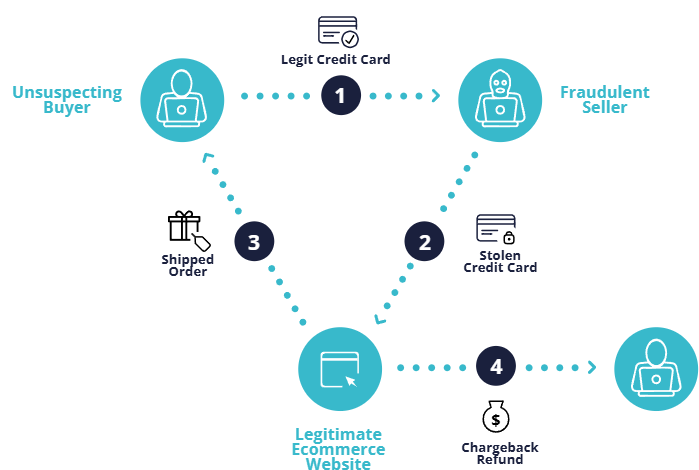
Step-by-step process of triangulation fraud
Here is a typical walkthrough of how fraudsters execute triangulation fraud:
1. Genuine customer purchase: The genuine consumer purchases a product or service with genuine card details from what they think is a known seller (e.g. an eCommerce marketplace, booking websites, etc). In truth, they are buying from a fraudulent reseller. Criminals often advertise cheap and discounted products to attract buyers and communicate directly with the customer to earn the sale. As a result, a consensual transaction executes with a valid payment method. The fraudster pockets this “pushed” money.
2. Fraudulent ordering: Instead of shipping or fulfilling the customer’s order, the fraudster then places a second purchase with an honest merchant on behalf of the genuine customer. But for this second transaction, the criminal uses another innocent user’s stolen credit card data (often gathered from phishing, fraud rings, and friendly fraud schemes) even though the product delivers to the genuine customer’s address. By mixing real customer details with stolen payment data, the order appears legitimate to the merchant. Many scammers will go so far as to have full sales conversations with merchants, phone calls, or back-and-forth email chains.
3. Genuine order processing: The merchant, on the assumption they are working with a verified third party, processes the false payment and ships the product to the genuine customer. The customer receives what they paid for, has no idea they are part of a scam, and does not raise any alarms.
4. Final chargeback: Eventually, the owner of the stolen credit card notices unauthorized charges and files a chargeback against the merchant. The merchant, now liable for both the lost product and the payment, is left with little recourse and suffers a financial loss.

Triangulation Fraud Prevention Challenges
Triangulation fraud is a social scheme that exploits legitimate eCommerce systems. As a result, this type of fraud is particularly challenging to detect, and for several reasons:
- Complexity: Three-way fraud includes multiple parties and transactions mixed with fake and real payments. For example, it is very hard to determine the difference between a fraudulent travel agent and a real one — both are fulfilling a transaction on behalf of a genuine client. Fraudsters also enjoy a veil of anonymity as a transaction is broken into three decentralized legs that appear authentic, which makes catching the scam a challenge.
- Delays: Most fraud detection systems identify the scam days or weeks after the transaction executes, and only if repetitive activity is detected. Often, the scam only surfaces when a cardholder files a chargeback.
- Sophistication: Fraudsters use realistic business details (reseller pages, phone numbers, addresses, etc) mixed with stolen payment details obtained from data breaches, phishing, or account takeovers. That complexity makes it hard for customers and merchants alike to spot any deception.
- False positives: Since triangulation scams mimic honest sales (and plenty of eCommerce sites encourage third-party middlemen), many fraud solutions over-flag true transactions or make mistakes.
- Data silos: Effective detection requires collaboration among retailers, marketplaces, and card issuers. However, limited data sharing in the industry hampers timely intervention.
- Customer confusion: Customers often remain unaware of the scam, may not recognize signs of fraud, or fail to report suspicious activity as they receive the ordered products without issues.
Weaknesses of Triangulation Scams (and how you can use that to
protect your business)
Even though middleman fraud operates behind the scenes to conceal the scheme, some signs hint towards triangulation fraud. For one, triangulation fraud does have a digital trail. The fraudster uses stolen card details—once the legitimate cardholder or financial institution notices suspicious activity and reports it, you can trace the card and fraud origin. And if you collect order and transaction details from the middleman, that can lead back to the false reseller account. Second, triangulation fraud orders contain mismatched info and conflicting data. Orders from the fraudster occur with a device or location that does not match expected billing, shipping, or geographic data. Fake or incorrect drop addresses, suspicious IPs, strange email addresses, incorrect biometrics/device fingerprinting, and wrong geolocation data can all raise flags. Thirdly, criminals often work in groups and use repeat tactics to work their schemes at scale. In the case of triangulation fraud, criminals want products that will entice buyers, have a low profile to avoid detection systems, earn fast cash flow, and operate at high volume to limit risk. As a result, there are common reseller patterns that speak to the likelihood of triangulation fraud:
• Frequent, low-value orders
• Products with small margins and high turnover
• Bulk sales
• Popular items with high sales values
• High transaction volumes targeting resellable, movable, or returnable items
Lastly, there is metadata you can watch for that betrays a scammer. A lack of communication, changes in language style, strange payment activity, multiple accounts, missing or unverified account details, or unconventional shipping requests all hint towards a fraud ring rather than an honest consumer or reseller.
How FUGU Protects Your eCommerce Business With Post-Payment
Verification Processes:)
With a detailed understanding of the common triangulation signs, FUGU’s proprietary AI algorithms are uniquely prepared to defend against middleman fraud. We confirm the legitimacy of orders as the transaction occurs to reduce the risk of fulfilling orders made with stolen credit cards. We achieve this via post-payment tracking. The signs for triangulation fraud are apparent—if you have an adequate time runway and can assess the common signals of fraud against preset risk thresholds. For example, with triangulation fraud, there is often email communication between the fraudster and the customer or merchant. By looking through that communication data, we can detect middleman scams. A scammer can often betray their intentions (misplaced address details, evasive responses, last minute change requests).
Or if we notice that the location of the customer, third-party reseller, email/IP, and credit card details are all different, that hints toward triangulation fraud, which we can then explore. This only occurs with high-quality post-payment verification. The longer you monitor each incoming detail of a transaction, the more accurate a picture you build, letting you better detect triangulation fraud. FUGU accomplishes this goal through several tool features:
- Automated flagging and transaction lifecycle monitoring: We cross-reference data points over the entire transaction, not just at the end, long after the scam is complete. Accurately catch criminal triangulation activity from robust sets of data (powered by AI) while the scam occurs.
- Behavior risk profiling: Analysis of suspicious behavior triggers alerts when order activity surpasses preset risk profiles. Evidence of triangulation fraud is collected over time to prevent false positives on precise risk criteria (FUGU customers have seen a 41% decrease in false declines).
- Tailored disparate data points: FUGU searches for conflicting data typical of a middleman scam. That includes reseller patterns, verification discrepancies, and odd activity often not calculated with static fraud tools (e.g. lack of email openings, website return tracking, velocity checks going back and forth, etc).
- High-quality customer support: AI-enabled and expert service representatives, once alerted, work quickly to detect and limit triangulation fraud. Not only does that stop a fraudulent order from processing, it also lets merchants better reclaim lost funds due to chargebacks (FUGU holds a leading 61% chargeback recovery rate).
Card-not-present fraud (of which triangulation fraud is a sub-type) accounts for 73% of total card fraud. That has led to more than $30 Billion in global losses for 2022 alone, with estimates of yet greater losses in the future. Merchants and industry players must build adequate defenses to this type of fraud to ensure sustainable business health. Fortunately, emergent technology provides effective methods to track and limit triangulation fraud. By decoupling acceptance from verification and assessing transactions across the entire payment model, FUGU’s AI powered analysis can detect fraudulent triangulation orders before they process, helping protect revenues with far fewer false positives. To see how the tool works, check out our solutions page